Post-quantum cryptography to avoid the Quantum Apocalypse
Post-quantum cryptography to avoid the Quantum Apocalypse
A new review article 1 stresses out the necessity of the integration of new generation post-quantum cryptography protocols to industrial and critical infrastructures environments.
The exponential development of communication technologies in the late 20th century and, specially, in the early 21st century has resulted in a contemporary society that exists in a hyperconnected world. In this context, communications do not only refer to the actions of texting, phone (video) calls, social media or news media but also to the control of industrial machines, bank transfers, stock acquisitions, control of unmanned aerial vehicles or managing automated houses (domotics), to name a few. Strongly tangled concepts, such as Smart Cities, Industry 4.0, or the Internet of Things are currently being investigated for their convergence with other advanced technologies, such as artificial intelligence or quantum computing on a historical inflection point in the form of a fourth industrial revolution.
In this sense, relying on communications for executing the critical tasks involved in such hyperconnected paradigm requires that those transmissions of information are secure and private. Cyber vulnerabilities in the control systems of a smart city or an automated industry may lead to catastrophic consequences. For example, in a possible future where the transport of people and cargo is exclusively done by autonomous vehicles which rely on the communications among them and some central control stations to move around, the intrusion of a malicious entity on the system to disturb it would lead to fatal consequences economically and socially (casualties).
Hacking activities on critical infrastructures
Hence, modern crime and war is heavily based on hacking activities with the scope of manipulating critical infrastructures, to produce economical or social losses by interrupting their production or by decreasing the life-time of their devices, or obtaining sensitive information regarding state, industrial or personal secrets (banking information or sensitive images, for example). In 2022, there was an estimated amount of 2200 known cyberattacks per day, posing a threat to businesses’ infrastructure every 39 s. Importantly, not all the critical infrastructures of a country need to be attacked at once, the fall of some selected few may lead to a catastrophic propagation of failures through the whole network due to the interconnection among the elements.
All of these vulnerabilities make cybersecurity and cryptography to be today more important than ever. The core of their protocols resides in the fact that they are based on hard problems that cannot be solved in a practical time frame by classical computing methods, i.e., thousands of years of computing are required to extract the plain text from the ciphertext if the key is unknown. Unluckily, quantum computers pose a threat to the security of those asymmetric cryptography protocols. A “Quantum Apocalypse” that would result in sensitive data and systems to become completely vulnerable is a possibility not to be neglected.
Post-quantum cryptography
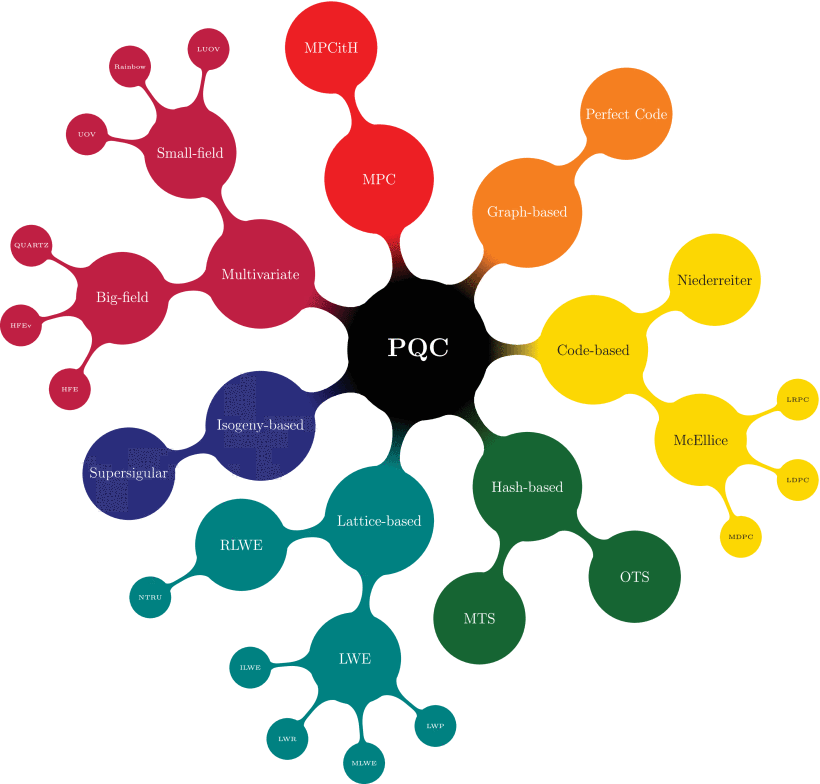
Here is where post-quantum cryptography comes into play. Post-quantum cryptography has been proposed as the paradigm of classical cryptography schemes that are secure against attackers that have access to fault-tolerant quantum computers. Quantum computers do not provide an exponential speed-up to solve every computer science problem and, therefore, the main idea in post-quantum cryptography would be to find hard problems that cannot be efficiently tackled by such technology, even if it is fully operational.
Post-quantum cryptography is one of the most important topics in cryptography at the moment. Thus, there are many works pointing out the importance and the lack of cybersecurity in operational technology environments, as well as surveys about post-quantum cryptography systems. However, there is a gap in the literature regarding the merge of both problems.
In this review, the authors provide a comprehensive picture of the state-of-the-art of post-quantum cryptography from the perspective of industrial and critical infrastructures networks. For doing so, they focused on critical infrastructures networks, which are at the core of the supply of goods and services that are indispensable for providing social and economical necessities on a day-to-day basis.
The researchers conclude that although there are many different post-quantum cryptography alternatives that seem to provide good security against quantum attacks for information technology services in the near-future, their implementation in critical infrastructures is far from trivial. The absence of a general benchmark of post-quantum cryptography algorithms under the same conditions (e.g., same processor for latency tests) makes it hard to make a top view comparison among them to conclude which could be well suited for implementation in critical infrastructures networks. The authors discuss some points that stand out as the most relevant future research lines regarding this topic.
Author: César Tomé López is a science writer and the editor of Mapping Ignorance
Disclaimer: Parts of this article may have been copied verbatim or almost verbatim from the referenced research paper/s.
References
- J. Oliva del Moral, A. deMarti iOlius, G. Vidal, P. M. Crespo and J. Etxezarreta Martinez (2024) Cybersecurity in Critical Infrastructures: A Post-Quantum Cryptography Perspective IEEE Internet of Things Journal doi: 10.1109/JIOT.2024.3410702 ↩